Coverage for eBPF programs
- Track: LLVM devroom
- Room: D.llvm
- Day: Saturday
- Start: 14:00
- End: 14:35
- Video with Q&A: D.llvm
- Video only: D.llvm
- Chat: Join the conversation!
eBPF is fastly becoming the first choice for implementing tracing and security-critical applications and software.
Yet, its ecosystem lacks tooling to make developers' life easier.
Join this talk to get to know bpfcov: an open-source tool I wrote that uses the LLVM pass infrastructure to instrument your eBPF programs to collect coverage data while they run in the eBPF VM in the Linux kernel.
I bet we all have heard so much about eBPF in recent years. Isn't it?
Every day we hear about a new project using some eBPF magic underneath.
eBPF programs are written in C but compiled for a specific ISA later executed by the eBPF Virtual Machine.
LLVM has a specific backend allowing us to write C and get eBPF ELF objects out.
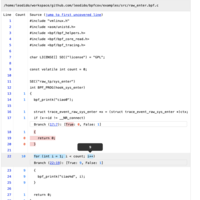
Still, there are no tools helping developers to clearly understand which path their code took while running, which branches were uncovered, and maybe why.
Even testing the eBPF programs is a pain, given that not all the types of eBPF programs are supported by BPF_PROG_TEST_RUN in the Linux kernel.
Yes, BTF and CO-RE are improving the situation. But, writing eBPF is still mostly about fighting against the BPF VM verifier.
Until today, there is no simple way to visualize how the flow of your eBPF program running in the kernel actually was.
That's why I sat down and wrote bpfcov. A tool to gather source-based coverage info from your eBPF programs.
During this talk, I will show the audience the secrets of the BPF target in LLVM and how I wrote an out-of-tree LLVM pass to instrument eBPF programs with counters, counters expressions, and friends.
The goal is to help eBPF developers to get to know how to use the powerful LLVM infrastructure to make the eBPF ecosystem - and their life - better.
Speakers
| Leonardo Di Donato |